
Security is not a feature. It's a foundation.
Explore practical, forward-thinking strategies to defend your business from modern threats. From MFA to phishing defense to risk assessments, Secured & Delivered covers the evolving landscape of cybersecurity—because security isn't optional, it's foundational.

Why ‘We’re Too Small to Be a Target’ Is the Most Dangerous Lie in Cybersecurity
"We’re just a small business. Who would want to hack us?"
A lot of folks still believe this.
And it’s the #1 reason small organizations get blindsided by cyberattacks.
Hackers don’t pick victims manually anymore.
They automate. They scan. They hit whatever’s easiest.

Security by Checkbox: Why Passing the Audit Isn’t the Same as Being Secure
Passing an audit is worth celebrating—but don’t confuse it with being secure.
In this post, we take a hard look at “checkbox security”—those environments that pass the compliance test on paper, while attackers quietly exploit the gaps in real life. From MFA that isn’t enforced to outdated “security training,” we walk through where things fall apart and what real security looks like beyond the spreadsheet.
If your last audit gave you a clean bill of health but you’ve still got nagging doubts, this one’s for you.

Fighting Fire with Fire: How AI Is Changing the Cyber Threat Landscape—And Your Defense Strategy
Artificial intelligence isn’t coming for your job—it’s already in your inbox, your SIEM, and maybe even that suspiciously perfect phishing email. In this post, we break down how attackers are using AI to get faster and sneakier—and how you can use it, too. But don’t expect a silver bullet. AI needs strategy, tuning, and a good human sidekick. If your incident response plan doesn’t include the bots, this one’s for you.
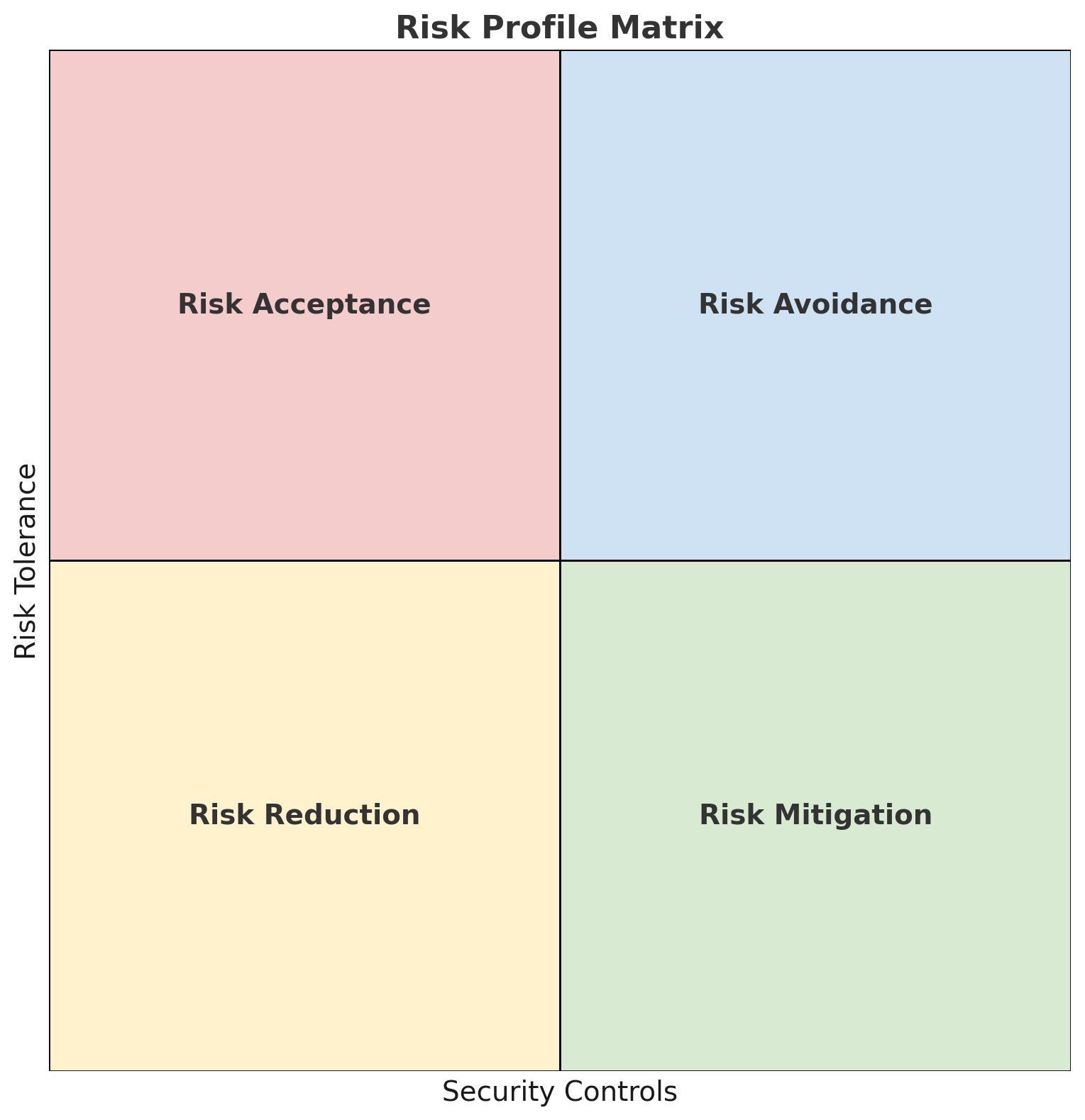
🛡️ Know Your Risk: Why Understanding Your Risk Profile Is the Key to Better Cybersecurity
Every organization faces risk—but not every organization should respond the same way. Discover how Ferrous Equine Technologies helps you define your risk profile and turn it into a clear, actionable cybersecurity roadmap tailored to your goals.

📊 Microsoft Secure Score: How It Works, Why It Matters, and How to Actually Use It
Secure Score is more than a number—it’s your Microsoft environment’s security blueprint. Learn how Ferrous Equine Technologies turns that score into real-world results through smart planning, risk alignment, and cross-platform context with Azure.

Introducing the Security Posture Review
🔍 Is your business truly secure—or just hoping for the best?
A Security Assessment isn’t just a checklist; it’s your roadmap to understanding real risks, spotting gaps, and getting ahead of threats before they hit. In this post, we break down what goes into a quality security assessment, what you can expect from the process, and how it empowers smarter decisions.
👉 Click to read how Ferrous Equine Technologies approaches cybersecurity with clarity, practicality, and impact.
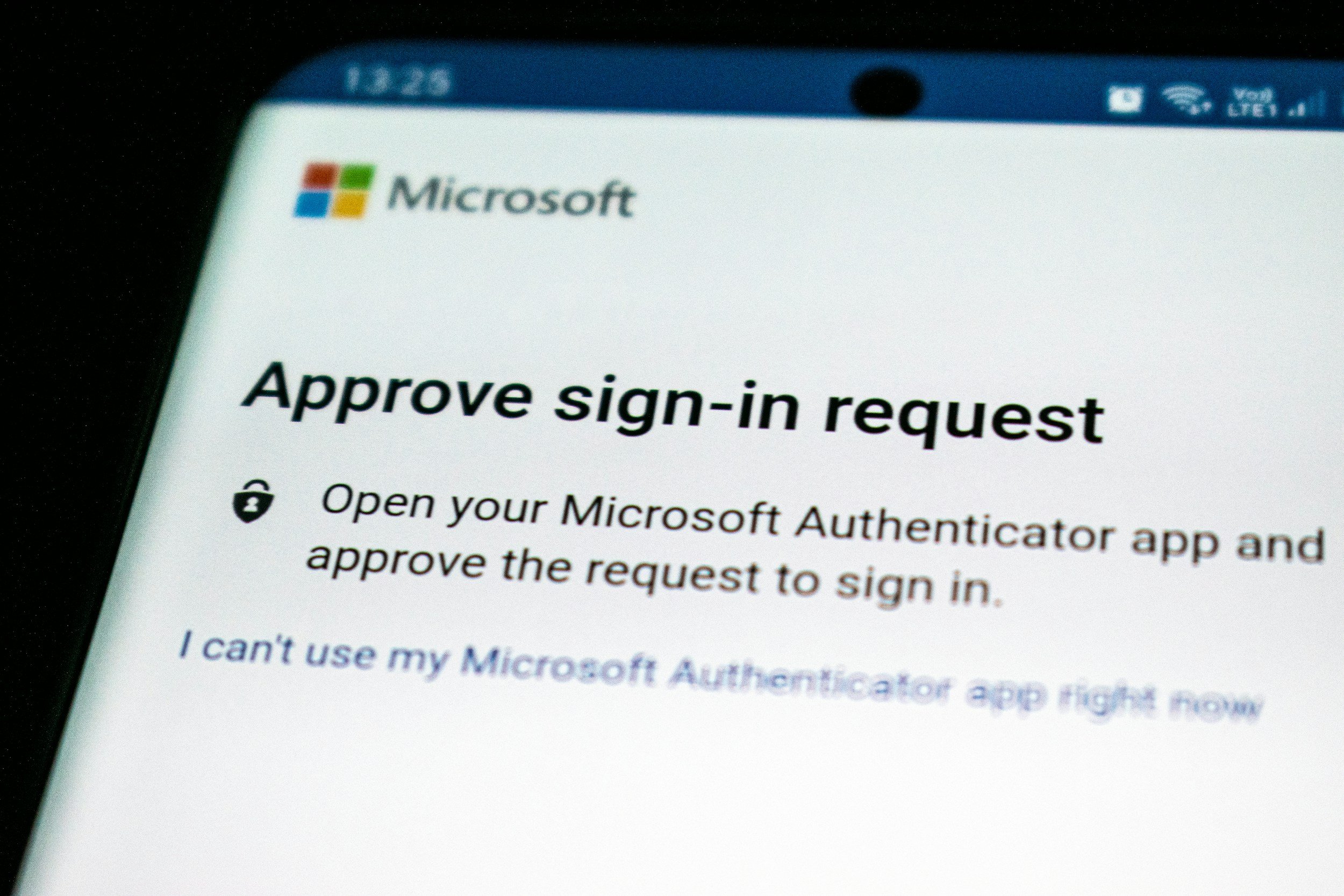
🔐 MFA or Bust: Why Passwords Alone Are a Cybersecurity Joke
Still relying on passwords alone to protect your business? That’s like locking your barn with a shoelace. In this deep dive, we break down why Multi-Factor Authentication (MFA) isn’t just recommended—it’s required. Learn how attackers bypass simple login setups, why MFA is the first step in any real security strategy, and how Ferrous Equine Technologies makes the rollout easy (and maybe even fun).

🧟♂️ Legacy Authentication: The Zombie Protocol Haunting Your Network
Think your MFA rollout means you’re protected? Think again. Legacy authentication protocols—like IMAP, POP3, and NTLM—silently bypass modern security controls and remain one of the most exploited gaps in cloud environments. This blog explains where legacy auth hides, how it undermines your zero trust efforts, and how Ferrous Equine Technologies helps you eliminate it without breaking your business.

